Is AI in cybersecurity an asset or a threat? Many IT professionals in Australia worry about using AI in cybersecurity, but AI technologist Amanda Johnstone sees it as a powerful defence tool. She shares her insights on how you can use AI to enhance your security.

In the world of cybersecurity, many people see Artificial Intelligence (AI) as a double-edged sword of risk and opportunity. A Capterra survey of 350 IT professionals in Australia found that 28% see AI-enhanced attacks as a top threat for their company over the next year.*
However, Amanda Johnstone [1], an AI technologist and TIME Next Gen Leader tells us AI can be just as powerful when used for defence instead of offence.

Johnstone says AI-powered features are increasingly common in IT management and security software, noting “what was once a Fortune 2000 privilege is now accessible to all."
The hard part now is choosing strategies and specific products that will maximise your company’s protections against rapidly evolving cyberthreats—especially if you run a lean team with limited security expertise. We’ve combined Johnstone’s recommendations with our takeaways from new Capterra surveys of IT pros in Australia to help you bolster your security.
The full methodology that we’ve used for those two surveys is at the bottom of this article.
1. Assess your defences: are you ready for AI-enhanced threats?
“AI advancements—including deepfakes and voice cloning—are sophisticated enough to fool even experienced IT professionals,” notes Johnstone.
Many companies are already adapting to meet this challenge, with a Capterra survey finding that 66% of IT and security professionals in Australia have developed specific measures to defend against AI-generated deepfake attacks at their companies.**
“I am surprised that not everyone is defending against AI-generated deepfake attacks,” says Johnstone. “100% of companies should develop measures to defend against this; it should be something that we're all thinking about straight off the bat. Compliance and risk mitigation are paramount for businesses that store financial and health information, or data about people who are underage, like schools, for example. And when we consider industries like real estate, banking, education, health, defence, retail, and telecommunications, they're all really vulnerable to cyber attacks,”
For many small and midsize enterprises (SMEs), limited resources and outdated security practices increase their vulnerability—especially given the variety of ways cybercriminals are applying AI.

Your first step to increased protection is to audit what you’re currently doing and using. If your business relies on a basic IT management system without additional protective measures, more than that may be needed to fend off these threats. Johnstone advises that businesses should not assume default features in IT management software cover them.
“To fix cybersecurity vulnerabilities, remove the shame [of being unprepared or fooled] and ensure people have not only financial resources but also the right tools and decisions at their disposal,” says Johnstone.
She emphasises these critical strategies to strengthen your security posture:
- Don't make assumptions: Companies must not rely on default features in IT management systems to cover them. Policies, training, and tools that haven't been updated in years leave a gap. “Every business must be prepared for cyber attack one day… It's not a matter of ‘if’ but ‘when’," Johnstone advises.
- Review your policies regularly: Johnstone emphasises, "Companies must regularly reassess IT vulnerabilities. Removing shame and ensuring people have not only financial resources but also the right tools and decisions are crucial". Regular updates to IT policies and tools are essential to staying ahead of evolving threats.
- Engage a cybersecurity professional or consultant: For businesses struggling to keep up with evolving threats, Johnstone recommends hiring external help. “Compliance guidelines vary by data type and industry, but every organisation should hire an expert—whether a consultant or a CISO—when addressing or investing in cybersecurity," Johnstone advises. Engaging a professional ensures your business’s unique risks are thoroughly assessed and tailored solutions are implemented to close any security gaps.
By following these guidelines, small businesses can transform their IT management systems into a more comprehensive line of defence, minimising risks and staying ahead of potential threats.
2. Boost your defences: upgrading to advanced AI software
“AI’s role in cybersecurity is evolving from reactive to proactive, identifying potential threats and even predicting attacks before they happen,” says Johnstone.
If you’ve determined your current tools and processes aren’t enough to deal with new cyber threats, look for software vendors that incorporate AI to detect and respond to threats in real-time. Advanced network monitoring systems with AI can identify unusual patterns, while generative AI can quickly pinpoint the root cause of network issues. According to Gartner’s Predicts 2024: AI & Cybersecurity—Turning Disruption Into an Opportunity [2], AI-enhanced tools provide continuous threat exposure management (CTEM), which not only helps businesses stay ahead of threats but also reduces the response burden by validating potential risks through simulations and predictive analytics.

When vetting a platform, here are some questions to ask vendors:
- How does your product use AI to enhance security?
- Can your software detect and adapt to new threats autonomously?
- Are there predictive features in the solution that help anticipate attacks before they happen?
AI-driven cybersecurity solutions can help teams adapt to quickly evolving threats by analysing vast amounts of data across the network in real-time. These systems can automatically adjust security protocols based on threat intelligence, identify patterns of potential attacks, and anticipate vulnerabilities before they are exploited. This dynamic risk management includes features like automated threat prioritisation, which evaluates the severity and business impact of each risk, and attack path mapping, which analyses possible routes attackers could take through a network. AI’s ability to continuously learn and refine these assessments helps security professionals prioritise high-risk exposures and respond immediately, minimising potential damage. [2]
As Johnstone notes, AI’s continuous learning ability means all day and night, improving the accuracy of threat detection, an essential feature for businesses that need round-the-clock security without employing a 24/7 team.
3. Seeking expertise: how agencies can enhance your security
“When reassessing IT operations, engage a professional to guide you. Develop a risk matrix that involves the entire senior leadership team, understand your client base, and reverse engineer from there. When vetting an agency, avoid consultants who can't simplify their explanations. They should be able to explain things clearly—like to a 10-year-old—and guide leaders at all levels without judgement," Johnstone says.
The complexity of modern threats often requires specialised knowledge from an external expert. Of the most powerful services these agencies can provide is a vulnerability assessment to identify weak points. According to Gartner's 2024 Strategic Roadmap for Managing Threat Exposure [3], vulnerability management should evolve into a continuous threat exposure management practice, focusing on broader organisational risk rather than just individual technical vulnerabilities.
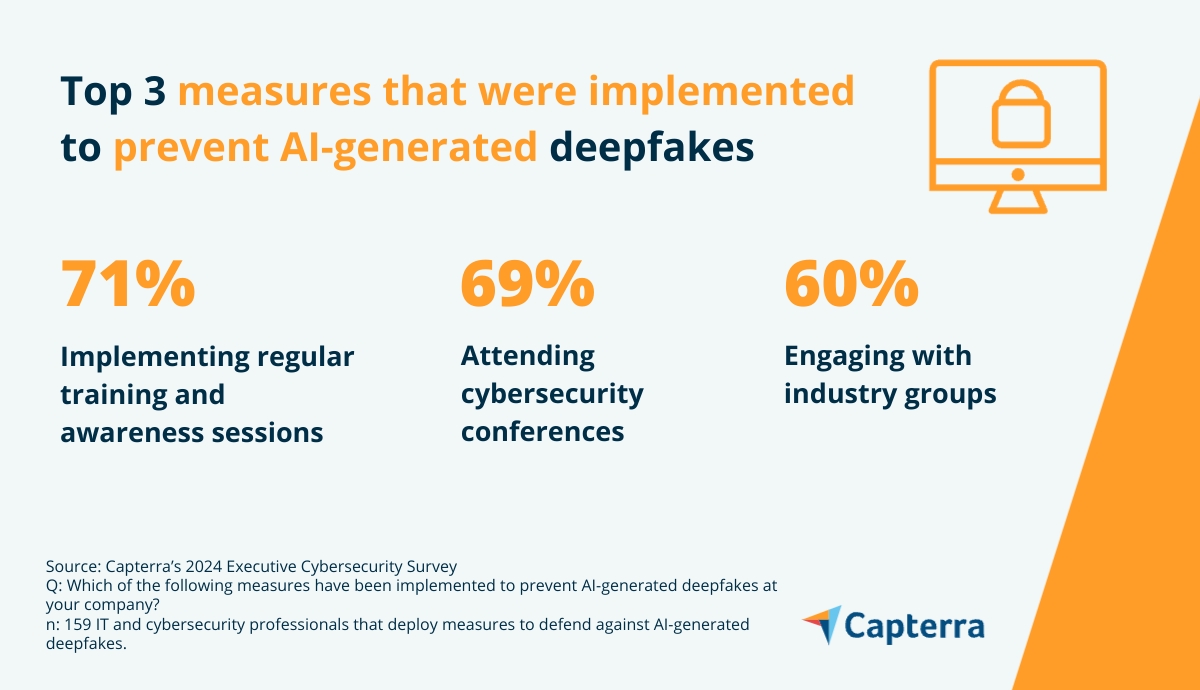
In a recent Capterra survey, of IT and cybersecurity professionals in Australia who indicated that their companies have developed measures to defend against deepfake fraud: 71% have implemented regular training and awareness sessions, 69% attend cybersecurity conferences, 60% engaged with industry groups, and 47% implemented simulation exercises*.
If you don’t have the resources internally to take these kinds of steps, seek a managed security provider or consultant to help guide your cybersecurity strategy. Many can even arrange simulation exercises like the one shown below.
Transforming AI into an ally: last steps for business security
AI is transforming the landscape of cybersecurity, both for attackers and defenders. For small businesses, understanding how to turn AI into an ally can mean the difference between becoming a victim and staying protected.
"Cyberattacks are a certainty, not a possibility. Founders and executives must prepare now, as the likelihood of facing a breach is nearly 100%," says Johnstone.
Johnstone’s insights remind us that while the threats are real, the tools to combat them are within reach. By reviewing your current defences, upgrading your software with advanced AI capabilities, and bringing in expert help when needed, your business can turn AI into a powerful asset.
Here’s how you can take action:
- Reassess your defences: Regularly review IT policies and systems to stay updated against evolving threats.
- Leverage AI: Upgrade your tools to include AI-enhanced capabilities to predict and respond to threats.
- Consider expert help: When in doubt, hire a consultant or MSSP to guide your strategy and fill in the gaps.
With the right setup, AI can be one of your strongest allies in the fight against cybercrime.
Survey methodology
* Capterra’s 2024 Annual Data Security Survey aimed to learn more about data security practices in businesses around the world. The survey was conducted online in August 2024 among 350 respondents in Australia.
Respondents were screened for full-time employment in an IT role with responsibility for, or full knowledge of, their company's data security measures. This report displays the results based on 4,000 respondents.
**Capterra’s 2024 Executive Cybersecurity Survey was to explore how IT and cybersecurity professionals are responding to the rising threat of biometric fraud. The survey was conducted in May 2024 among 241 respondents in Australia.
Respondents were screened for IT and cybersecurity roles at companies that use security software and have more than one employee. Respondents were screened for involvement in, or full awareness of, cybersecurity measures implemented at their company. This report displays the results based on 2,648 respondents.
Sources

